Understanding Multi-Factor Authentication (MFA) and its importance in today’s world
Meet Multiple Factor Authentication (MFA), the ultimate security solution that adds an extra layer of protection to your login process. In today’s world, where cyber threats are at an all-time high, protecting your online accounts has never been more critical.
Our last article left off with the idea of added security steps to protect your data beyond the heavily guarded password vault. Hackers are getting smarter every day, and people continue to make avoidable mistakes.
According to security.org, 25% of password managers reuse their master passwords on other sites. Your business must be one step ahead of everyone else. Well, at least two or more, that is.
The different types of MFA and how they work
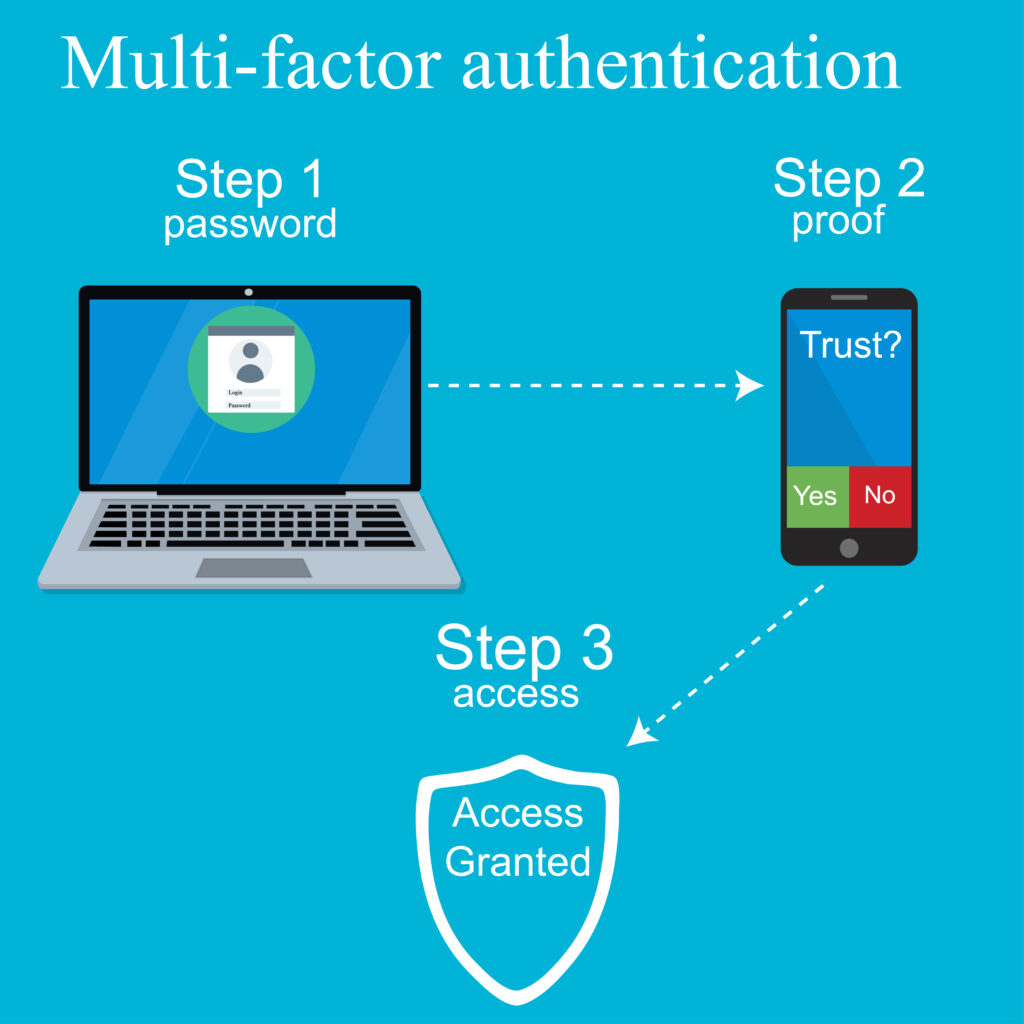
Multi-Factor Authentication (MFA) adds added layers of safety to your log-in procedure. MFA in your everyday life is more familiar to you than you think. If your log-in prompts a code sent to your phone to input, you have experienced 2 Factor Authentication (2FA). Or someone hacks into your system, they will not have access to this code. If you lose your phone or it is stolen, added layers, if chosen, protect you further.
A third later is known as biometric authentication and proves something you are. A perfect example is when your phone uses Face ID to access a website. As you know, it does not work for anyone else but you. It proves that you have the right to enter a particular system and are who you say you are.
Setting up MFA
Suppose you were to think of a non-technology scenario where the concept of MFA occurs. How about the VIP section of a venue? After conquering the first step of the busy front door with identification, another layer of security is needed to gain access to the VIP section. You can only come in if you know the secret password. This venue tends to use the same passwords as their other locations, so you try the earlier one that worked last weekend and it worked! Innovative thinking on your end, not theirs.
The outcome might not have been the same if there had been a third layer of protection, such as having your name on a VIP list.
Now back to technology. With all these layers, you are entirely safe, correct? Unfortunately, as we will continue to mention throughout our blog series, security breaches will persist. That means some hackers can get through the layers, but the more you have, the harder it will be.
Next up, learn about security breaches and what you need to know.





