In today’s rapidly evolving digital landscape, the security of sensitive financial data has become of utmost priority for accounting professionals. The consequences of a data breach might be catastrophic for your firm. These include financial losses for your clients, damage to your reputation, or erosion of client trust in your firm. Every industry needs IT support, but IT support for accountants is mandatory in order to keep everything safe & for hassle-free operations.
Does your accounting firm have the proper security in place? If not, you need to collaborate with an expert IT support team. Having the proper security measures in place is an indispensable component for any accounting firm seeking to fortify their defences and uphold cyber-safe accounting practices for themselves and their clients.
Sandra Network, an IT Support company in Peabody and Boston, is such an IT company. We possess a deep understanding of the distinctive requirements of accounting firms. Our team offers them comprehensive solutions designed to strengthen their data security and we can offer them to your firm too.
The Importance Of Data Security In The Accounting Industry
In this digital-centric era, data breaches have become a reality posing a significant threat to accountants and accounting firms. One of the most common causes of these data breaches in this industry is the theft or loss of laptops and other electronic devices. These devices hold a treasure trove of proprietary and sensitive client and corporate information. You don’t want a data breach to potentially be a catastrophe for your firm. And if it happens, it can unfold in the blink of an eye.
Especially disheartening is that if a data breach happens to your firm, the accountability most likely will fall on the accountant or the firm making you responsible for any resulting losses and/or damages to your clients. These situations also escalate quickly into class action lawsuits with hefty fines making it challenging for a firm to recover.
The impact often goes beyond financial implications. It can affect the loss of your firm’s reputation in the industry and the loss of your client’s trust in your firm. This loss of industry reputation and client trust can inflict far greater damage. Accountants rely heavily on the trust and confidence of their clients to thrive, and even a single breach can shatter years of hard-earned credibility. The aftermath of a data breach casts a dark shadow over the reputation and integrity of accountants and firms, creating an uphill battle to restore trust and rebuild relationships.
At Sandra Network, we recognize the gravity of these challenges and the high stakes involved. Our aim is to empower accountants and accounting firms with the knowledge and resources needed to fortify their defences and protect against the constant threat of data breaches. With our expertise and unwavering commitment to data security, we equip our clients with the tools and strategies necessary to navigate this treacherous landscape with confidence.
Be pro-active. Don’t let the future of your firm’s reputation hang in the balance. Safeguard its reputation, preserve your client’s trust, and secure your valuable data in the face of the ever-present risks of the digital world.
Since 2014, reported data breaches of CPA firms have increased by over 80%, and, since 2018, the portion of breaches that include ransomware or extortion has risen to over 40%.
The Crucial Role of IT Support in Data Security
In the realm of data security, the indispensable role played by IT support cannot be overstated. When it comes to safeguarding sensitive financial information, you need to partner with a Managed IT service provider, one who possesses specialized knowledge and expertise for accounting is paramount.
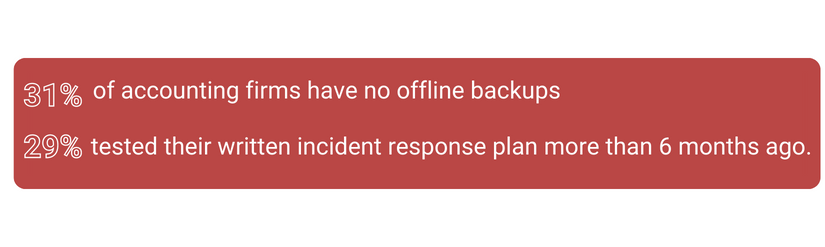
At Sandra Network, we understand the unique challenges faced by accountants and the critical importance of protecting their valuable data. By collaborating with our dedicated team of IT experts, accountants gain access to industry-specific insights and solutions. Our professionals have an in-depth understanding of the accounting landscape, enabling them to assess vulnerabilities, identify potential weak points in systems, and develop tailored strategies that enhance data security.
With proactive monitoring and advanced threat detection mechanisms, we stay one step ahead of cyber threats, ensuring potential risks are mitigated before they escalate. The significance of IT support in data security is underscored by statistics revealing that over 90% of successful cyber-attacks stem from human error or system vulnerabilities. By partnering with us, accountants substantially reduce their susceptibility to such attacks, minimizing the potential for financial losses and reputational harm.
At Sandra Network, we implement robust security measures, including advanced firewall management, real-time antivirus support, and state-of-the-art encryption techniques. By continually monitoring your network and promptly responding to any potential threats, we ensure the safety of your sensitive financial data. In a rapidly evolving digital landscape, entrusting your data security to expert IT support is not just a wise decision—it is a necessary one.
In a rapidly evolving digital landscape, entrusting your data security to expert IT support is not just a wise decision—it is a necessary one.
By relying on professionals who comprehend the unique challenges faced by accountants, you can have peace of mind, knowing that your data is safeguarded while you concentrate on your core responsibilities. Take the proactive step to fortify your defences and partner with Sandra Network to harness the power of IT services for accounting firms in protecting your sensitive financial information.
Strengthening Defences: Key Components of IT Support for Accountants
At Sandra Network, we understand the unique needs of accountants when it comes to IT support. Our comprehensive range of services is designed to provide accountants with the necessary tools and expertise to ensure data security and operational efficiency. Here are the key components of our IT support for accountants:
- Customized IT support and security solutions tailored to the unique needs of accountants.
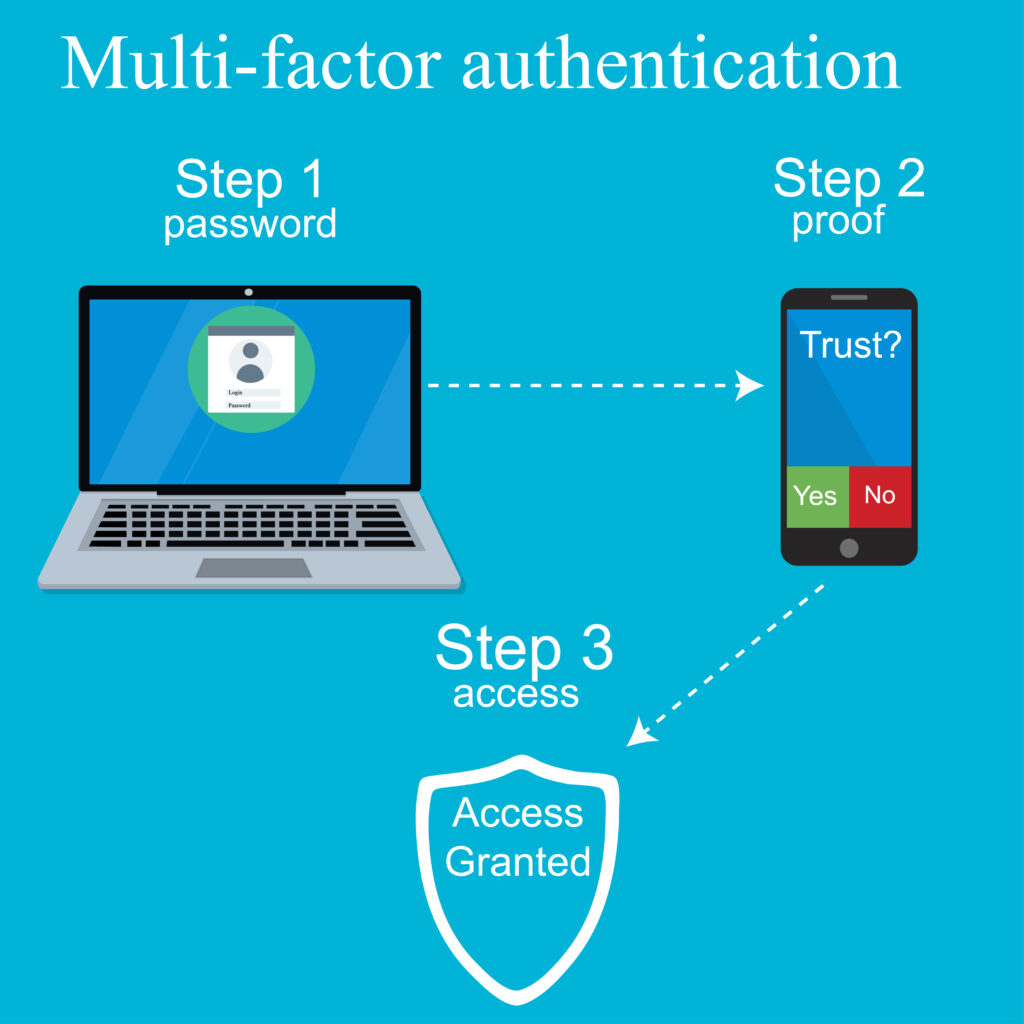
- Essential security measures, including firewall management, antivirus support, and encryption techniques, to protect sensitive financial data.
- Proactive network monitoring, threat detection, and incident response plans to identify and address potential security threats.
- Employee training and awareness programs to educate and empower staff about cybersecurity best practices.
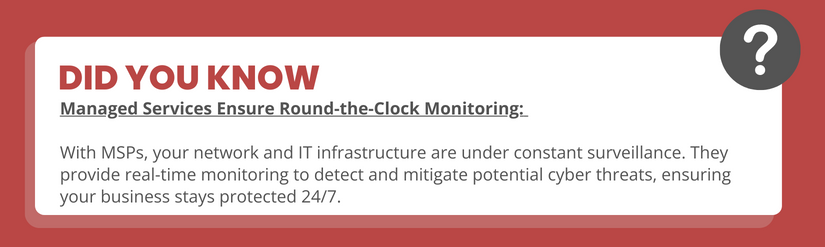
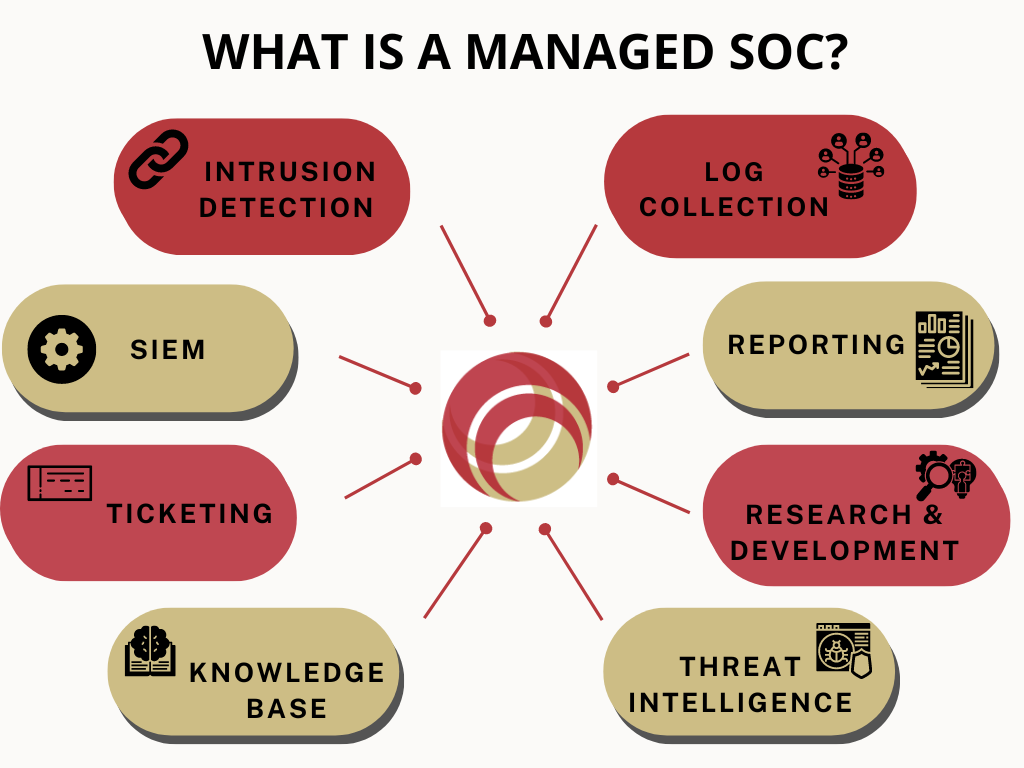
- Advanced security operations services, including 24×7 security monitoring and incident response, to ensure round-the-clock protection.
- Proprietary process to identify vulnerabilities and provide targeted training, going beyond standard phishing awareness.
- Quick and efficient resolution of IT issues, crucial for time-sensitive accounting operations.
- White glove approach to IT structure and security, offering ongoing protection and support.
- Expert advice and support from experienced IT professionals who understand the accounting industry.
- Comprehensive suite of services, including cloud solutions, hardware sales, web hosting, and more.
- Responsive support, especially during critical periods like tax season.
Customized Solutions: Meeting the Unique Needs of Accountants
At Sandra Network, we understand that accountants operate in a highly regulated industry with specific requirements and compliance standards. We recognize the importance of tailoring IT services for accounting firms to meet the unique needs of accountants, providing them with the tools and expertise necessary to navigate the intricacies of their profession.
The global average cost of a data breach between July 2018 to April 2019 was $3.92 million. For larger organizations, the average cost was $5.11 million, whereas for smaller organizations with between 500 and 1,000 employees, the average cost was $2.65 million.
One of the key aspects of our customized solutions is our deep understanding of the accounting industry’s compliance standards. We stay up to date with the latest regulations to ensure that our clients remain in full compliance with industry requirements. By addressing these specific compliance needs, we help accountants maintain the integrity of their data and safeguard their clients’ sensitive information.
To address industry-specific challenges, we offer a range of specialized software, tools, and protocols that enhance data security for accountants. For example, we can assist in the implementation of secure document management systems that protect sensitive financial information and facilitate seamless collaboration within accounting teams. Our team is well-versed in encryption techniques and can deploy advanced security measures to safeguard data both at rest and in transit.
Furthermore, we understand the importance of maintaining a robust network infrastructure for accountants. Our IT support services include network monitoring and threat detection, allowing us to identify and respond to potential security breaches promptly. We can also develop tailored incident response plans to minimize the impact of any security incidents and ensure business continuity.
Accountants rely on specialized software for their day-to-day operations, and we have the expertise to recommend and support the tools that best suit their needs. Whether it is accounting software, tax preparation applications, or financial management systems, we can ensure seamless integration, optimal performance, and data security.

By offering customized solutions that address the specific requirements and challenges faced by accountants, we empower them to focus on their core responsibilities with the confidence that their IT infrastructure is secure and efficient.

The Benefits of Partnering with Expert IT Support IT Support For Accountants
When it comes to managing data security, accountants often find themselves burdened with numerous responsibilities. Partnering with an expert IT support company, such as Sandra Network, can alleviate this burden and provide peace of mind. Our team of dedicated professionals takes on the task of managing data security, allowing accountants to focus on their core responsibilities and deliver exceptional services to their clients.
One of the key benefits of partnering with professional IT support is the potential for cost savings and efficiency gains. By leveraging our expertise and specialized tools, accountants can streamline their operations, reduce downtime, and increase productivity. With proactive monitoring, timely updates, and efficient troubleshooting, we ensure that their IT infrastructure remains optimized and reliable, minimizing the risk of disruptions or costly data breaches.
Furthermore, our team at Sandra Network stays at the forefront of emerging technologies and industry trends. We continuously evaluate the evolving threat landscape and implement proactive measures to stay one step ahead of cybercriminals. Our commitment to ongoing training and knowledge ensures that our clients benefit from the latest advancements in data security.
By partnering with an expert Managed IT services company servicing accountants, your firm can enjoy the benefits of streamlined operations, enhanced data security, and a trusted partner that understands your unique needs. At Sandra Network, we are dedicated to empowering accountants with the tools and support they need to thrive in today’s digital landscape.
Conclusion:
In this blog post, we have explored the crucial role of IT support in ensuring data security for accountants. We began by highlighting the evolving cybersecurity threats faced by the accounting industry and the potential risks and consequences of data breaches. We emphasized the importance of partnering with expert IT support to fortify defences and establish cyber-safe accounting practices.

Understanding the unique needs and compliance standards of the accounting industry is paramount when it comes to safeguarding sensitive financial information. IT support plays a vital role in tailoring solutions to address industry-specific challenges, offering specialized software, tools, and protocols that enhance data security for accountants. By partnering with a trusted provider like Sandra Network, accountants can benefit from customized solutions that align with their specific requirements.
The benefits of partnering with Managed IT services for accounting are significant. Not only does it alleviate the burden of managing data security, but it also leads to potential cost savings and efficiency gains. By entrusting data security to professionals, accountants can focus on delivering exceptional services to their clients while ensuring the reliability and integrity of their IT infrastructure. Real-world examples and case studies have showcased the positive impact of expert IT support on accountants’ cybersecurity posture, emphasizing the value of such partnerships.
In conclusion, prioritizing data security is of utmost importance in the accounting industry. Accountants must recognize the risks involved and take proactive measures to protect their clients’ sensitive information. Seeking professional IT support, such as Sandra Network, can provide the necessary expertise, resources, and ongoing support to establish robust data security measures. By partnering with us as your trusted IT support provider, accountants can safeguard their reputation, maintain client trust, and navigate the digital landscape with confidence.

Remember, at Sandra Network, with our IT Services for Accounting Firms, we are committed to empowering accountants with comprehensive IT support and tailored solutions. Your clients’ sensitive information deserves the highest level of protection, and we are here to ensure that you can focus on what you do best while we manage your data security needs.
.