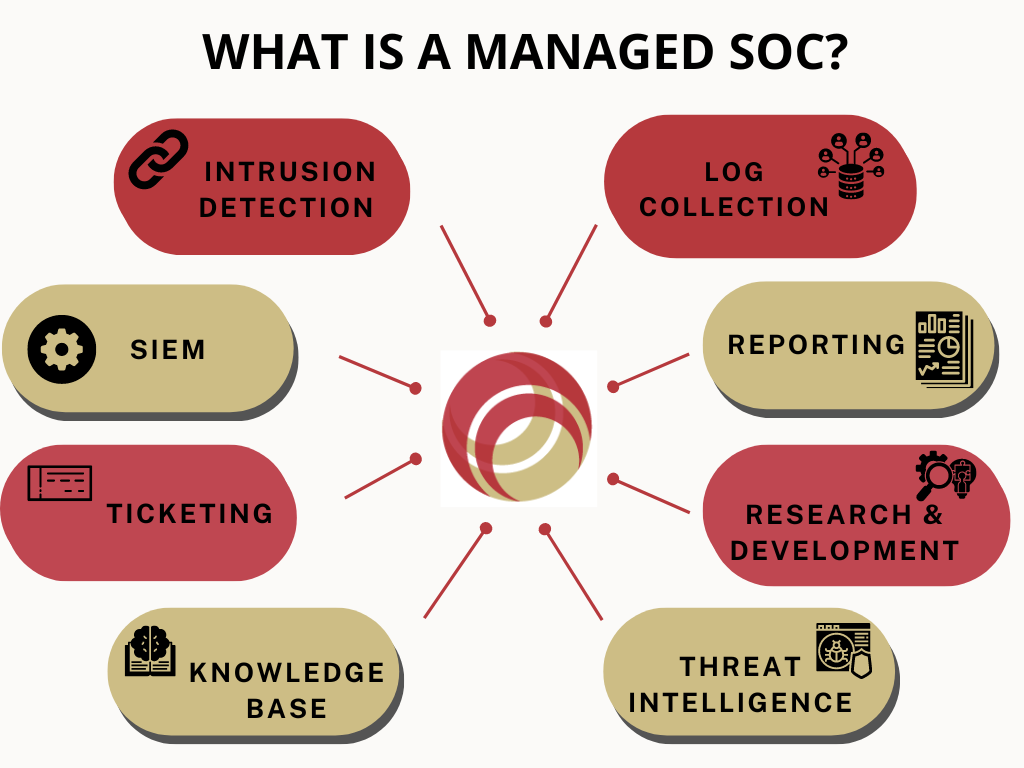
What is a Managed SOC? Understanding the Basics of Security Operations Center Management
Welcome to the world of cybersecurity! With the rise of digital threats, it’s more important than ever for businesses to keep their data and systems safe. One of the best ways to do this is by having a Security Operations Center (SOC). But what exactly is a SOC, and how can it help protect your business?
In this blog post, we’ll explore the basics of SOC management and introduce you to the concept of a managed SOC. Whether you’re a small business owner just starting to consider cybersecurity measures or a seasoned IT professional looking to enhance your security strategy, this post will provide you with a solid foundation for understanding the importance of a managed SOC.
So, grab a cup of coffee, sit back, and let’s dive into the world of cybersecurity together!
Introduction
As a small or medium-sized business owner, it’s vital to protect your business from cyber threats. A key element of any cybersecurity strategy is a Security Operations Center (SOC), a centralized facility that provides 24/7 monitoring, detection, and response to security incidents.
In this blog post, we’ll introduce you to the concept of a managed SOC, and explain how it can benefit your business. We’ll provide essential information for those new to cybersecurity, and take a deeper dive into the benefits of a managed SOC and what you should consider when selecting a provider. By the end of this post, you’ll have a solid understanding of the basics of SOC management, including the key components, benefits, and best practices. Let’s explore how a managed SOC can help safeguard your business from cyber threats, and how Sandra Network can help you every step of the way.
Does Your Business Need a Managed Service Provider?
In today’s fast-paced and tech-driven business landscape, the question arises: Does your business need a managed service provider (MSP)?
The answer is a resounding yes! A managed service provider can be a game-changer for your business, offering a wealth of benefits and expertise that can propel your operations to new heights. From ensuring the security and stability of your IT infrastructure to providing proactive monitoring and support, an MSP brings a wealth of knowledge and resources to the table.
By partnering with an MSP, you gain access to a team of dedicated professionals who specialize in managing and optimizing your technology systems, allowing you to focus on your core business objectives. Say goodbye to the headaches of managing your IT internally and embrace the strategic advantages that come with partnering with a trusted managed service provider.
Your business deserves the peace of mind, efficiency, and competitive edge that only an MSP can provide.
What is a SOC?
A Security Operations Center (SOC) is a centralized facility that provides 24/7 monitoring, detection, and response to security incidents. Its primary purpose is to identify and mitigate cybersecurity threats to your business, including both internal and external threats. Cybersecurity professionals staff a SOC and utilize specialized tools and techniques to monitor network activity, detect potential security incidents, and respond to security threats as quickly as possible.
The key components of a SOC include people, processes, and technology. The people component includes cybersecurity professionals who are responsible for monitoring and responding to security incidents. The processes component includes documented procedures for identifying and responding to security incidents, while the technology component includes tools and technologies used to monitor network activity and detect potential security incidents.
Benefits of having a SOC
- Continuous monitoring and rapid response to security incidents to minimize the damage caused by cyber-attacks.
- Compliance with regulatory requirements for data security, particularly for businesses in heavily regulated industries.
- Enhanced visibility into security events and potential threats, allowing for proactive threat hunting and faster incident response times.
- Reduced risk of business disruption, financial losses, and reputational damage resulting from cyber attacks.
- Increased confidence and trust from customers and partners due to a demonstrated commitment to protecting sensitive information.
- Improved incident detection and response, which helps to identify and mitigate security incidents more quickly and effectively.
- Greater efficiency and effectiveness in managing security incidents, resulting in reduced downtime and faster recovery times.
- Access to specialized cybersecurity expertise and tools that are often cost-prohibitive for businesses to develop and maintain in-house.
Managed SOC vs. In-House SOC
As a business owner, you have two options for managing your SOC: you can either build an in-house SOC or outsource your SOC to a managed SOC provider. Each approach has its own pros and cons, and the right choice for your business will depend on a range of factors.
Managed SOC vs. In-House SOC: What’s the Difference?
An in-house SOC is a facility that is built and maintained by your business. Your own cybersecurity professionals staff an in-house SOC and are responsible for monitoring, detecting, and responding to security incidents, whereas a managed SOC is an outsourced facility run by a third-party provider. The provider is responsible for monitoring, detecting, and responding to security incidents on your behalf, using their own cybersecurity professionals and tools.
Pros and Cons of Each Approach
In-House SOC
Pros:
- Complete control over your security operations
- Direct access to your own cybersecurity team
- Easier to tailor to your specific business needs
Cons:
- Requires significant upfront investment in infrastructure, staffing, and training
- Ongoing maintenance costs can be high
- May lack the expertise and tools available from a specialized managed SOC provider
Managed SOC
Pros:
- No upfront investment required
- Access to specialized cybersecurity expertise and tools
- Lower overall maintenance costs
Cons:
- Reduced control over your security operations
- Less direct access to your cybersecurity team
- May require some level of integration with existing IT infrastructure
- Factors to Consider when Choosing Between Managed SOC and In-House SOC
When choosing between a managed SOC and an in-house SOC, you should consider a range of factors, including your business size, industry, regulatory requirements, and budget.
An in-house SOC may be a better fit if you have significant security needs and resources to invest in, while a managed SOC may be a better fit if you have limited resources or want access to specialized cybersecurity expertise and tools.
Ultimately, the right choice for your business will depend on your unique needs and circumstances.

Get a Free Risk Assessment
How Does a Managed SOC Work?
A managed SOC is an outsourced cybersecurity service that is designed to help businesses detect, analyze, and respond to security incidents.
It operates by providing around-the-clock monitoring of your IT infrastructure and applications, using advanced tools and technologies to identify and alert your team of any security threats.
How Does a Managed SOC Operate?
A managed SOC operates by collecting data from across your IT environment, such as logs, network traffic, and other security events. Advanced security tools and techniques are used to analyze the data and identify potential threats, which are then escalated to your team for further investigation and response.
The managed SOC team provides a range of services to help protect your business, including vulnerability assessments, threat intelligence, incident response, and compliance management.
Services Provided by a Managed SOC
A managed SOC provides a range of services to help protect your business, including:
- Continuous monitoring of your IT infrastructure and applications
- Real-time threat detection and alerting
- Vulnerability assessments and risk management
- Incident response and remediation
- Compliance management and reporting
- Threat intelligence and analysis
- Security awareness training for employees
Benefits of Using a Managed SOC
By using a managed SOC, you can benefit from:
- 24/7 security monitoring and incident response
- Access to specialized cybersecurity expertise and tools
- Faster incident detection and response times
- Reduced risk of business disruption and financial losses
- Improved compliance with regulatory requirements
- Enhanced visibility into security events and potential threats
- Increased confidence and trust from customers and partners
Moreover, at Sandra Network, we offer a comprehensive managed SOC service that is tailored to your unique business needs. Our team of experienced cybersecurity professionals will work with you to develop a customized security strategy, that addresses your specific risks and requirements.
With our managed SOC service, you can have peace of mind knowing that your business is protected around the clock from evolving cyber threats.
Managed SOC Best Practices
Working with a managed SOC provider can be an effective way to ensure that your business is protected from cyber threats. To get the most out of your partnership, consider the following tips:
- Choose a provider with a strong track record of delivering high-quality services.
- Clearly define your security requirements and expectations in your service level agreement (SLA).
- Regularly communicate with your provider to ensure that they are aware of your evolving business needs and security priorities.
- Provide your provider with access to your IT environment and security policies and procedures.
- Conduct regular reviews of the provider’s performance against the SLA and make necessary adjustments.
At Sandra Network, we work closely with our clients to understand their unique business needs and security objectives and develop a customized security strategy that aligns with their goals.
We provide around-the-clock security monitoring and incident response, leveraging the latest security tools and technologies to ensure that our clients are protected from cyber threats.
Our clients have access to a team of experienced security experts who are dedicated to keeping their IT environment safe and secure.
Understanding the importance of cybersecurity is essential for businesses of all sizes. In addition to utilizing a Managed SOC, there are other measures that companies can take to protect themselves from cyber threats. For example, implementing a password vault and working with a managed service provider can also enhance your organization’s security.
Conclusion
As cyber threats continue to evolve and become more sophisticated, it’s crucial for businesses to prioritize cybersecurity and take proactive measures to protect their assets.
A managed SOC provides businesses with 24/7 security monitoring, access to cutting-edge security tools and technologies, and a team of expert security professionals.
We at Sandra Network are committed to assisting our clients in safeguarding their businesses against cyber threats. If you would like to learn more about our managed SOC services, please visit our website or contact us to schedule a consultation.
Don’t wait until it’s too late – take action now to protect your business with a managed SOC.